| |
Protect Your Business - Take a Pro-Active Approach to Employee Computer Monitoring
Monitoring employee e-mail, internet and electronic communications isn't a big brother tactic; it's smart business. Employee use of company computer resources can open any organization up to electronic risks. To help control the risk of litigation, security breaches and other electronic disasters, employers should take advantage of technology tools to battle people problems - including accidental and intentional misuse of computer resources.
Increase Productivity & Protect Company Resources
When it comes to workplace computer use, employers are primarily concerned with inappropriate use of internet, e-mail, personal blogs, instant messaging, etc. The KEYKatcher Magnum is well suited to track these activities as well as time spent at the keyboard. Since the KEYKatcher Magnum is so easy to implement, you have the flexibility and swiftness to target possible threats without cumbersome software installation and configuration.
The Best Defense is a Good Offense
Having a plan in place is essential to counteract the risks of inappropriate use of computer resources. Creating and enforcing a clear, acceptable use policy (AUP) is crucial for employers to protect their assets.
Tips for Taking Appropriate Action to Mitigate Potential Risks:
Prepare · Develop clear and concise policies for computer use.
Implement · Install Magnum on every computer you want to monitor.
Monitor · Play back the stored data to determine if any inappropriate activity is taking place. Magnum’s Time/Date Stamps and innovative Time of Use Charts tell you when the computer was or was not in use.
Resolve · Confront alleged compromise with factual documentation. Determine potential risks and take appropriate action.

Magnum Keyloggers are Loaded With These Powerful Features:
128-Bit Encryption
We're serious about data security. The KEYKatcher Magnum features 128-bit AES (Advanced Encryption Standard) encryption for maximum security. The same data security that is commonly used for banking transactions keeps your data safe and secure.
Time/ Date Stamping
It's about time! Know when activities are taking place. KEYKatcher Magnum has built-in time/date stamping with an internal battery back-up. Accurate time is maintained even when the computer is turned off, or the device is unplugged.
Time of Use Charts
Our computer use charts show you at a glance when the computer is being used. Who was using your computer at 3 am on a Saturday morning? Was Joe at work last Friday? These questions and more are quickly answered with our convenient time of use charts. (See screen shot below.)
4 Megabytes of Data Storage
We're serious about storage. The KEYKatcher Magnum can store almost 4.2 million keystrokes. This is over 2,500 pages of text. Whether you're planning on writing a novel, or just looking to record for long periods of time, the Magnum has more than enough storage capacity.
TrueStampTM Technology
TrueStamp technology makes it virtually impossible to falsify time/ date stamps. This extra level of security leaves no doubt about when activity occurs (See screen shot below.)
Records Data at the Source
KEYKatcher keyloggers records keystrokes as they are typed for maximum accuracy and reliability. Software is vulnerable to detection and being deleted. Our secure hardware keystroke recorders step around the rat's nest of software to ensure system stability and ease of installation.
Pause on Playback
Everyone needs a break sometimes. When viewing activity, just press any key to pause the playback. When it is paused, press 'x' to exit, or any other key to view more activity. (See screen shot below.)
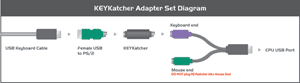
Purple Plug & Play Installation
The KEYKatcher is essentially a tape recorder for your keyboard. Just plug it in and it will start recording automatically. No software to install, and no directories to create. Easy to install and easy to use.
Set-Up Instructions
With no software to install, KEYKatcher products are really easy to use. The Magnum is even easier with Set-up instructions built-in to the menu.
Quick Erase
Erasing memory takes about 4 seconds - faster than other KEYKatcher products.
Multiple Viewing Options
Timestamps are great for knowing when activities take place, but can make text difficult to read. Viewing options make it possible to also view text as it was typed without the distraction of extra characters. (See screen shot below.)
Custom Password
A customizable password allows you to change the password from the default to a password of your choice.
NETPatrolTM Search
All KEYKatcher products feature NETPatrol for quick and easy identification of web addresses. NETPatrolT automatically identifies all occurrences of http, www., ".com", and ".net" along with surrounding text. At a glance, you can know what web addresses have been typed on your computer.
Keyword Search
Our powerful search utility allows you to search the memory without downloading the data. Searches save time and allow you to quickly piece together activities.
Battery Meter
Our battery level indicator shows the remaining battery life for peace of mind.
|